In this quick post I’ll show you how to add PowerShell v7 stable and preview releases to the new Windows Terminal.
<Update 2020-07-20>Originally this post was written for PowerShell v7.0.0-preview.1 before it was generally available. Since that time PowerShell v7 now has stable releases but continues with preview releases as well. I’m updating this post to reflect how you can add stable and preview releases side-by-side in Windows Terminal.</Update>
Background
The new Windows Terminal was announced at Build this year and has been available (building from source code yourself) through the Microsoft/Terminal GitHub repo. A very early preview of the Windows Terminal is now available through the Microsoft Store (link). I haven’t verified but I believe you’ll need a few prerequisites in order to install. Out of the box the current preview of Windows Terminal supports a number of shells including:
- PowerShell (v6, also known as “PowerShell Core”, and v7)
- Windows PowerShell (v5)
- CMD (command prompt)
- WSL (Windows Sub-system for Linux)
- Azure Cloud Shell
- and more…
Dynamic Profiles
By default, Windows Terminal now uses a feature called “dynamic profiles” to automatically generate profiles for any of the following shells on your machine:
- PowerShell
- WSL
- Azure Cloud Shell
At any time, you can remove (or rename if you want to keep a copy) the settings.json file used by Windows Terminal. This will force auto-generation of a new settings.json file so that you can see which shells it finds. Read more in the support article on this topic.
Dynamic profiles in Windows Terminal
https://docs.microsoft.com/en-us/windows/terminal/dynamic-profiles
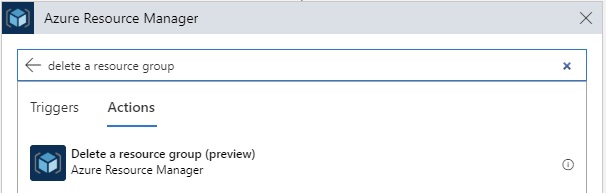
Solution
After installing the Windows Terminal from the Microsoft Store, open the Settings from the dropdown menu (or click “Ctrl + ,”).
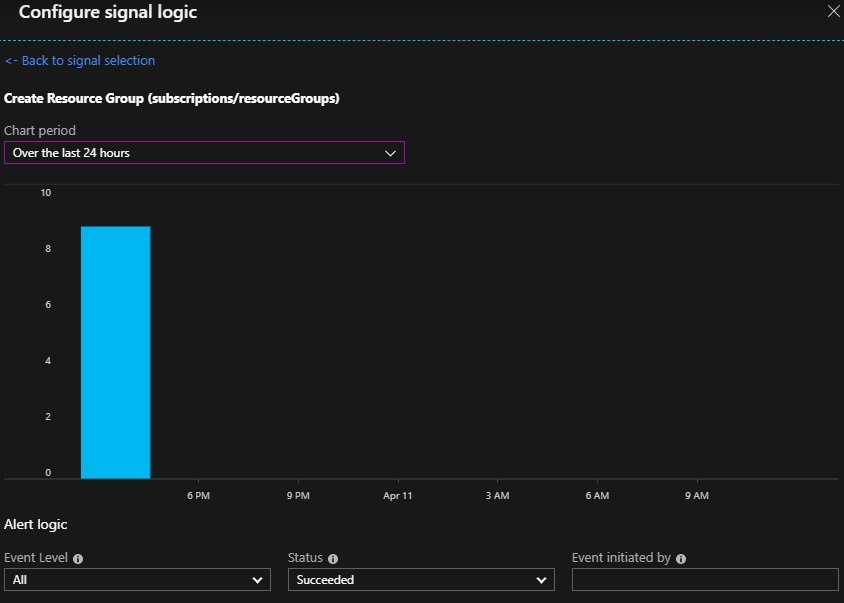
Find the “profiles” element in the settings file and add the following JSON snippet to the array. Verify the “commandline” and “icon” locations match where PowerShell v7 preview is installed on your machine.
{
"guid": "{574e775e-4f2a-5b96-ac1e-a2962a402336}",
"name": "PowerShell 7",
"fontFace" : "Cascadia Code PL",
"source": "Windows.Terminal.PowershellCore",
"hidden": false
},
{
"commandline" : "C:\\Program Files\\PowerShell\\7-preview\\pwsh.exe",
"fontFace" : "Cascadia Code PL",
"guid" : "{90cbdc15-f4fe-49d2-a245-ec066b70845f}",
"icon" : "C:\\Program Files\\PowerShell\\7-preview\\assets\\Powershell_av_colors.ico",
"name" : "PowerShell 7 preview",
"startingDirectory" : "%USERPROFILE%",
"hidden": false
},
Here is a link to my complete profiles.json for comparison.
After you’ve added the above element you’ll now see PowerShell v7 preview in your dropdown list of available shells with the proper icon.

Below screenshot shows PowerShell v7 Preview in use and verifying the PSVersion.

Bonus – Zsh and Oh My Zsh
For an added bonus I also added Zsh (with the Oh My Zsh framework for auto-suggestions and more) based on seeing demos from Jeff Hollan showcasing that shell.
Bonus – Cascadia Code PL
You may have noticed from the samples above that my shell profiles are using fontFace of “Cascadia Code PL”. Cascadia Code is a new font from Microsoft that was developed alongside Windows Terminal. The “PL” (Powerline) variant includes ligatures that take combinations of characters and convert them into glyphs. This is best demonstrated when you view the following documentation to see a sample. Note that there is some additional work (link) to configure this on your machine.
Cascadia Code
https://docs.microsoft.com/en-us/windows/terminal/cascadia-code
Conclusion
I’m very excited to begin using the Windows Terminal more in my daily tasks. Being able to switch back and forth between multiple shells (specifically PowerShell v5 and v6/v7) is possible in Visual Studio Code but this will be a much easier solution for many of my scenarios. Hopefully someone else will find this helpful as well.
-Frog Out